The Impact of Let's Encrypt Changes on Android Users
Let's Encrypt recently announced that it is moving to using its own root certificate on January 11, 2021. This will reduce operating costs and complexity for Let's Encrypt, helping their mission to make all websites secure by default.
December 21, 2020: Let's Encrypt have now announced a solution to resolve this issue and prevent any impact to Android users!
The potential footprint for this change is huge: Let's Encrypt DV certificates are used on 225 million websites at the time of writing. You and I, however, are unlikely to be impacted in our daily browsing: the new root certificate that will be used was added to browsers in 2017. This means that if you have updated your device in the past three years it will have the new root certificate installed.
Devices that have not been updated since the root certificate was released will not trust certificates issued against it, so older devices will simply not load websites that use certificates issued after January 11, 2021. This is an issue for a couple of device categories: Android and set top boxes (like your Smart TV). Android devices older than version 7.1.1 do not have the new root certificate, STBs are harder to define. Who doesn't update their device in three years, you might think. Unfortunately, Android device updates must be pushed by individual manufacturers (in the majority of cases) and devices that are carrier-locked further require the carrier to push updates. Some manufacturers and carriers may have decided to simply stop supporting older devices. System updates may also be too large for users on limited data plans to even consider downloading.
What's the impact
Globally, 12% of hits from Android tracked in mPulse were from unsupported versions (i.e. <7.1.1) in data sampled in November 2020. This figure varies dramatically by country, though:
Some stand out country statistics from the interactive map above:
- United States: 8.2%
- United Kingdom: 14.2%
- Brazil: 16.2%
- Russia: 17.0%
- India: 14.6%
- China: 9.6%
The data is not exhaustive, and is only measuring hits that identify themselves as Android on websites instrumented with mPulse. The outcome is startling nonetheless.
In some countries over 25% of Android devices will not trust Let's Encrypt certificates issued in 2021.
Do you use Let's Encrypt?
If you don't know whether your current certificate is from Let's Encrypt, because you use a third-party service such as a CDN or hosting company, you can check in your browser:
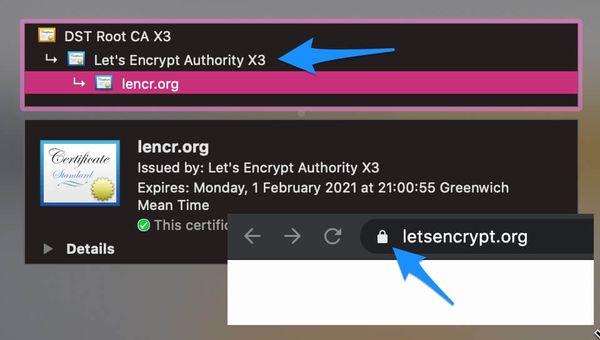
What you can do about it
Let's Encrypt provides advice to site owners. The gist is that although certificates will start to use the new, less compatible root certificate in January, you can force the old certificate until September. If you use certbot then you just need to use the flag --preferred-chain "DST Root CA X3", for example.
Other than delaying the inevitable until September 2021, there is nothing that can be done except for switching certificate providers or encouraging your users to install Firefox for Android, which uses its own, updated set of root certificates.
As for the other device categories, such as STBs, I would love to hear what folks are doing to prepare for the coming TLS-pocalypse.