The Performance Cost of EV Certificates
Introduction
Extended Validation or EV Certificates were once prized for their impression of increased security. Sites with an EV certificate would be rewarded with a nice green padlock and their company name in the address bar, potentially giving customers an increased sense of security when making purchases or entering sensitive data.

If you load a page on a domain with an EV certificate now, you will notice there is no longer a nice green padlock and the company name. This change rolled out in Chrome 77 way back in September 2019. Other browsers have followed suit, now a secure page (using any certificate type) will have a small indicator, normally a padlock, and non-secure pages will be highlighted as Not Secure.
The rise of free certificates
There are three primary types of certificate used to secure web traffic:
- Domain Validation (DV) validates that the certificate requestor owns the domain
- Organisation Validation (OV) validates that an organisation owns the domain
- Extended Validation (EV) validates that an organisation owns the domain, with rigorous validation
DV certificates just require you to prove that you own a domain: using a DNS record, a redirect or a file on your web server. This process can be completely automated. EV and OV certificates require some manual intervention and further checks at renewal.
The screenshots from Chrome below show the information provided to the user for these different certificate types.
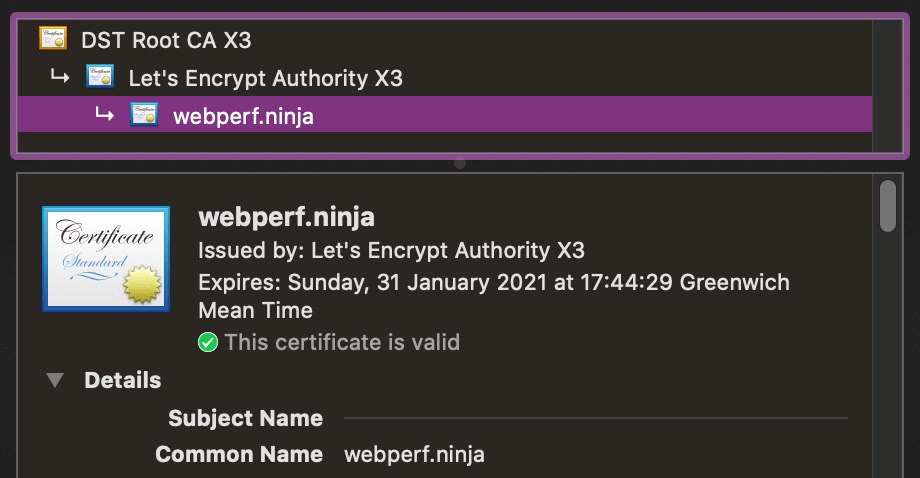
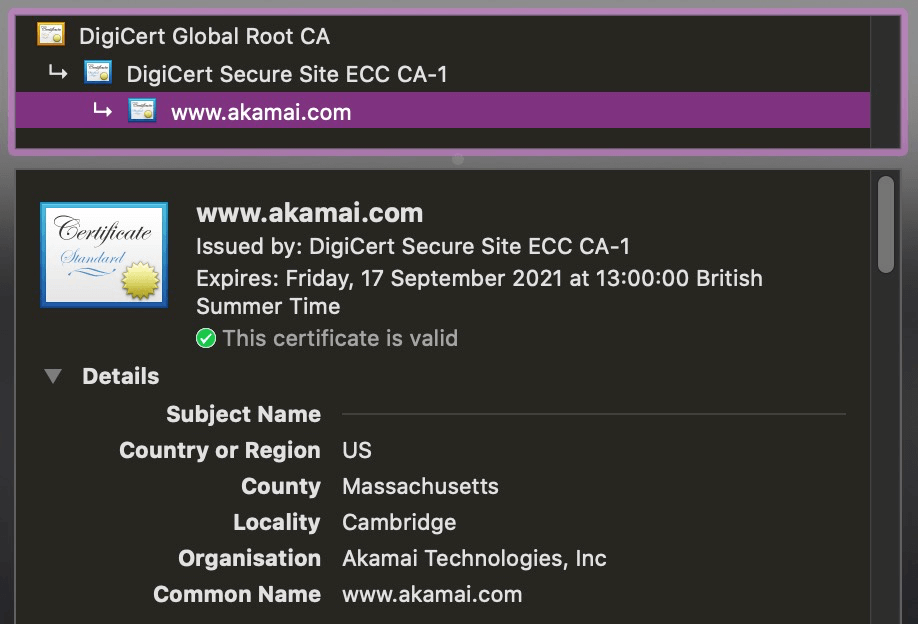

Making the web secure by default is an initiative I wholly support. Let's Encrypt is a non-profit certificate authority which allows any website owner to create a DV certificate for free. This makes it easier than ever to deliver pages over secure connections - preventing man-in-the-middle attacks and allowing the use of HTTP/2 which only works over TLS. Let's Encrypt is already integrated into most hosting providers and CDNs.
Extended Validation certificates are expensive; they require a legal entity to prove that they own the domain which requires some human intervention. At the time of writing, this results in an EV certificate costing about $125 USD per year. This is not a huge cost, but is infinitely more than free!
So what's the problem?
The performance challenge of EV certificates is that they do not fully support OCSP stapling. The online certificate status protocol is a method which allows clients like web browsers to ensure that certificates are valid, by checking with the certificate authority that it has not been revoked. Stapling allows the web server to perform this validation on the server-side and send the validation with the certificate. Without stapling the client has to do the validation. This can be seen in your web performance waterfalls as one or two (or more!) requests which occur during the TLS negotiation of the connection.
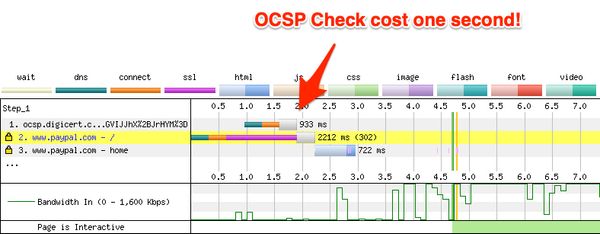
This abridged waterfall shows a webpagetest run at 3G speed against PayPal.com. The OCSP revalidation check takes almost a full second, over half of the TTFB for the response and 42% of the whole response.
This effect is more pronounced on high-latency connections. The latency here is not just based on the network connection, but also the distance between the user and the OCSP service. Digicert in this case uses Verizon's CDN which has 165 global points of presence (PoPs). Users in Western Australia, most of Africa, Canada and the former Soviet Union will have worse experiences than those in Europe and the United States.
As pointed out by Robin Osborne - there are no OCSP resolvers in China. This means that visitors could have up to a one minute delay before they load your page for the first time, and due to the fact that OCSP status is stored for seven days - this delay will occur once per week for each user!
A European client of mine recently switched from EV to OV and saw a significant performance improvement in TLS negotiation and thus Time to First Byte. The median negotiation time improved by 20% and it halved at the 95th percentile. Note the drop across all percentiles in this mPulse chart!
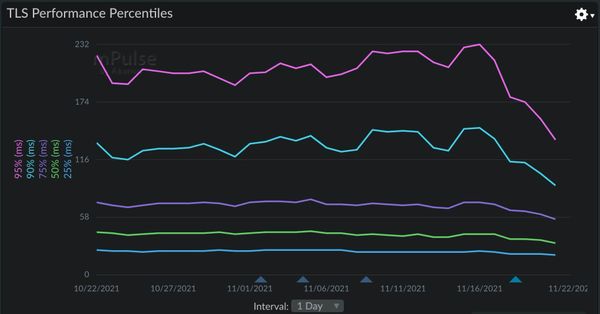
It is likely that moving from an EV certificate to organisation validation (OV) certificate will reduce costs and improve performance.
Note that OCSP stapling must be enabled on your TLS terminating endpoint (e.g. your firewall or CDN) for it to work on DV and OV certificates. You can check your current certificate using the Qualys SSL Server Test.
For simplicity I have ignored some of the intricacies of how OCSP works with intermediary certificates, and some of the many edge cases that occur with OCSP stapling. Matt Hobbs goes into much more detail in his blog post on certificate revocation if you crave more technical detail!